- O Filme dos Espíritos (Joel Pizzini, 2011)
- Cartas Para Julieta (Gary Winick, 2010)
- Copacabana (Marc Fitoussi, 2010)
- Os Goonies (Richard Donner, 1985)
- Coders at Work: Reflections on the Craft of Programming
- Família Vende Tudo
- Qual Seu Número? (Mark Mylod, 2011)
- Depuração de emergência: receita de bolo
- Trabalhar Cansa (Juliana Rojas, 2011)
- Despedida em Las Vegas (Mike Figgis, 1995)
- Vida e Software
- O Manuscrito Perdido (José Barahona, 2010)
- Roubando Vidas (D. J. Caruso, 2004)
- A Morte de Pinochet (Bettina Perut, Iván Osnovikoff, 2011)
- Aleksander Sokurov: Uma Questão de Cinema (Aleksandr Sokurov, 2011)
- Nervos à Flor da Pele
- O Desaparecimento do Gato (Carlos Sorín, 2011)
- As Flores de Kirkuk
- Là-bas: Educação Criminal
- Laços Humanos
- Cerejeiras em Flor
- Jovens Modernos
- Demônio
# O Filme dos Espíritos (Joel Pizzini, 2011)
Caloni, 2011-10-08 <cinema> <movies> [up] [copy]O Filme dos Espíritos é mais uma tentativa de "catequizar" (com o perdão da palavra) ou talvez educar os fiéis dessa crença religiosa da vida após a morte, dando sequência ao bom "Chico Xavier" e o desastroso As Mães de Chico Xavier. Aqui, porém, a alçada propagandista ganha contornos bem maiores que sua qualidade como filme, o que, de certa forma, lembra Olga, uma obra com o mesmo estigma. Dessa forma, o uso do cinema como ferramenta "educativa" se torna um completo desastre quando constatamos que toda essa ambição ideológica anti-aborto não se justifica em uma produção de caráter e gosto duvidosos.
A primeira impressão, logo nas primeiras cenas, é estar assistindo a uma obra ou 1) experimental, que irá jogar com técnicas inusitadas de movimento de câmera ou 2) amadorística, fruto de cursos de estudo de vídeos para a televisão. Infelizmente, embora uma vez ou outra o longa pareça se esforçar em se tornar de fato um filme, se dando ao luxo de inserir planos-detalhe que expliquem por si só o andamento da história (como o copo de cerveja na cama, ou as duas alianças juntas no mesmo dedo), o amadorismo começa a dominar cada vez mais a mise en scene, chegando ao ápice de aplicar os conhecidos bordões de mostrar a cidade amanhecendo em câmera acelerada (três vezes!) ou o efeito tremido e difuso para explicar o estado alcoolizado de um personagem. (Nada contra o uso de clichês, que podem ser úteis em muitas obras, mas tudo contra o seu mau uso, o que acaba aumentando mais ainda a sua banalização.)
Porém, confesso que o detalhe técnico que mais me angustiou durante toda a projeção foi justamente a fotografia pedestre, que não consegue dar conta da luz natural nas cenas externas, estourando luz muitas vezes, e não consegue manter uma uniformidade nos ambientes fechados, mesmo que esses ambientes nunca mudem. Contudo, seu amadorismo só se torna de fato evidente quando "admiramos" os enquadramentos completamente equivocados usados pelo diretor: vagos, genéricos e totalmente desinteressantes, muitas vezes olhamos para um jardim por massacrantes segundos que em nada contribuem para a já equivocada narrativa, que insiste em marcar o tempo simplesmente tornando as cenas maiores do que deveriam.
Para ajudar, a trilha sonora segue bombardeando qualquer traço dramático que possa existir na relação entre os personagens, lembrando muitas vezes as conhecidas vinhetas nada originais usadas nos cortes de cena das novelas televisivas. Porém, até essas vinhetas muitas vezes possuem uma composição dramática equilibrada, enquanto em O Filme dos Espíritos ela parece determinada a se identificar melhor com aqueles vídeos de casamento caseiros ou DVDs de auto-ajuda.
Como se não bastasse esse show de horrores, o filme tem a audácia de ir contra o aborto baseado em suas próprias crenças religiosas, retrocedendo décadas de compreensão científica a respeito da origem da vida. "Ora, mas é um filme religioso! Seria óbvio ele pregar seus dogmas, não?" Claro. Porém, em uma atitude desinformada, um dos personagens, médico, em uma das falas tenta associar a visão científica e aproximá-la (!) com a sua visão religiosa e ainda assim, continuar condenando o aborto e utilizando expressões como "justiça divina", que por si só revelam o verdadeiro (mau) caráter desse filme.
Não há nada no verdadeiro Cinema contra filmes religiosos que defendam seus dogmas. Diversos filmes nacionais foram lançados que mereceram algum destaque, como o já citado Chico Xavier e o mais recente Aparecida - O Milagre. Porém, infelizmente esse não é o caso. Apenas o que temos aqui é um vídeo propagandista que insere a questão do aborto em seu núcleo narrativo de forma simplista e covarde, se escondendo atrás de leis religiosas escritas por um obscuro doutor há cerca de 150 anos atrás, cuja produção possui mais defeitos que virtudes. Ou seja, é um raro caso de produção cinematográfica duplamente descartável.
# Cartas Para Julieta (Gary Winick, 2010)
Caloni, 2011-10-10 <cinema> <movies> [up] [copy]Sophie e Victor estão noivos e vão passar uma "pré-lua-de-mel" na Itália, onde Victor (García Bernal) pretende conseguir contatos com fornecedores para o restaurante que pretende abrir. Enquanto isso, Sophie (Seyfried) se desilude com as supostas férias e procura algo melhor para fazer: escrever respostas para as mulheres que lotam a frente da casa de Julieta, a mesma da peça de Shakespeare, com cartas românticas.
A interpretação costuma ser a base para o sucesso de filmes desse gênero, o que não vemos na carinha simpática, mas impassível de Amanda Seyfried (o oposto de Gael García Bernal, seu noivo, que resolve apelar para o overacting "nonsense"). Felizmente a aparição de Vanessa Redgrave na história como Claire, a autora de uma carta perdida de 50 anos atrás em que procurava manter contato com um amor da juventude e que agora busca reencontrar a pessoa que deixou para trás, consegue estabelecer um pouco de "felicidade" na narrativa, e mesmo a participação de seu mal-humorado neto (Egan) na empreitada consegue dar um pouco de ritmo na relação entre os três.
No entanto, a trilha sonora está disposta a estragar o que foi alcançado com uma seleção no mínimo inesperada (para não dizer inadequada). E por que não criticar a direção, que se esforça inutilmente em tentar criar algo mais para a nossa querida Sophie, mas que nunca é correspondida pela atuação de Seyfried.
Porém, o forte acaba sendo mesmo a atuação de Vanessa Redgrave que constrói, ainda que como coadjuvante, uma história muito mais tocante para ser seguida de perto.
# Copacabana (Marc Fitoussi, 2010)
Caloni, 2011-10-11 <cinema> <movies> [up] [copy]O novo trabalho do diretor-roteirista Marc Fitoussi faz um paralelo entre o estado de espírito de uma pessoa e o lugar onde esta vive. Para chegar a seus objetivos, rege de maneira impecável uma história em que as apostas que uma pessoa precisa fazer para chegar aonde quer não estão relacionadas com sua situação aparente, mas muito mais com seu estado interior e sua capacidade de transformar o mundo ao seu redor.
Esta é a história de Baubou (Isabelle Huppert), uma mãe que vive feliz de acordo com seus valores, mas descobre que não corresponde aos anseios da filha (Lolia Chammah), que dá muito mais valor às convenções sociais, tanto que acaba por colocar a própria mãe em segundo plano. Desacreditada, Baubou precisa provar para ela seu valor, e para isso arruma um emprego em lugar distante para refazer sua vida. Enquanto isso, a filha planeja seu próprio casamento, mentindo para seus sogros que sua mãe se encontra em uma viagem pelo Brasil, e que não conseguirá voltar para a cerimônia.
Só que o lugar onde Baubou realmente está se mostra frio e inóspito, não só pela sua aparência externa, mas pelas pessoas que lá habitam. Contratada para ser vendedora de apartamentos de veraneio, até seus colegas destoam totalmente de sua posição determinada e alegre, algo facilmente visto pela escolha acertada dos figurinos sóbrios do resto da equipe em detrimento à forma tresloucada de Baubou se vestir e se portar. Logo na primeira reunião entre eles, ela fica nitidamente apartada em um canto, e a câmera faz questão de isolá-la em algumas tomadas, exatamente para dar essa sensação de deslocamento.
Diante das dificuldades que ela precisa passar em seu novo emprego e sabendo que foi rejeitada pela filha, fica impossível não nutrir uma simpatia incondicional pelos esforços da protagonista para se firmar em seu novo habitat. Esforços esses que ocorrem de maneira completamente natural, mas que possuem o objetivo oculto de conseguir a filha de volta nos olhos da interpretação admirável de Isabelle Huppert, que não demonstra exageros em um personagem que poderia facilmente cair no ridículo, mas que ao invés disso termina por soar tão realista e presente de corpo e alma que aos poucos o resto das pessoas, incluindo sua própria filha, é que parecem inertes e alheias à vida.
O mais interessante é que nós mesmos, como espectadores, enquanto torcemos por ela, sabemos dos enormes riscos que ela corre de tudo não dar certo. E por isso mesmo suas ações parecem tão importantes, pois estabelecem essa nossa vontade de ter sucesso em nossas próprias ações do dia-a-dia, independente das dificuldades. A escolha da trilha sonora, adequadadamente acidental e que evoca a mentira da filha com compilações de MPB, não serve para as pessoas e o ambiente onde vive, e são fruto apenas da visão que a própria Baubou possui de sua realidade: uma visão muito mais otimista e alegre do que muitas pessoas gostariam de ter, mas que se escondem nas mesmas convenções que a sua filha tanto almeja.
Por isso mesmo é que seus triunfos possuem um gostinho de rebeldia delicioso, que cativa o público facilmente. E exatamente por acreditarmos em Baubou é que seu final inusitado não parece nem de longe inverossímil, mas sim é o complemento necessário da grande ideia para o filme: não sabemos o futuro, esse futuro que parece tão sombrio e tenebroso para muitas pessoas. Porém, independente disso, podemos apostar com todas nossas fichas, se acreditarmos de verdade em nós mesmos.
# Os Goonies (Richard Donner, 1985)
Caloni, 2011-10-13 <cinema> <movies> [up] [copy]"'Um grupo de meninos embarcam em uma aventura após encontrar o mapa de um suposto tesouro escondido.' É com esse argumento simples que se constrói um dos filmes mais empolgantes e divertidos dos anos 80. Essa é a união do roteirista Chris Columbus, de O Enigma da Pirâmide, do diretor Richard Donner, de Superman, e do idealizador Steven Spielberg, de... precisa dizer algo? Essa união produziu uma espécie de esfera criativa nunca antes vista, e que até produz ecos na filmografia contemporânea, em que o exemplo mais recente é o filme-homenagem Super 8, de J.J. Abrams."
Esse foi o primeiro parágrafo de meu texto de 2011. A seguir segue-se um monte de elogios para o filme, como detalhes da fotografia, atuações, edição e trilha sonora, com destaque para a música-tema de Cindy Lauper. A música-tema de Lauper continua sendo ótima, mas minha visão oito anos depois não. Os Goonies é um filme de Sessão da Tarde, mas isso não é demérito. Ele é divertido, previsível, engraçado. Tudo em alguns momentos. Este é um filme feito de momentos. E não só de momentos vive um filme.
Um grande filme deveria unir todos esses momentos em algo mais coerente ou menos clichê, mas ou o clichê alcançou os Goonies e eles não conseguiram se salvar em um filme que não conseguiu envelhecer se tornando algo a mais, ou minha persona de criança não conseguiu capturar a magia que muitos espectadores ainda devem ver nesse trabalho de Donner.
Talvez em uma próxima revisão mais velho...
# Coders at Work: Reflections on the Craft of Programming
Caloni, 2011-10-14 <books> <computer> interview> [up] [copy]"Personally I have never believed that it is possible to be a good coder without being a good programmer nor a good programmer without being a good designer, communicator, and thinker." - Jamie Zawinski
Como Joel e Atwood disseram, a leitura de Coders At Work é tão útil quanto ler o código dos outros, só que em um estilo mais condensado, que se aproveita das décadas de experiência dessa gente para aprimorarmos nossos processos de desenvolvimento e, muitas vezes, a forma de pensarmos sobre software.
No meu estilo de leitura circular, adaptada do brilhante (maluco?) método de Dmitry Vostokov, as coisas vão mais devagar, e estou apenas no início do livro, tendo passado por Jamie Zawinski (desenvolvedor da equipe original do Netscape), Brad Fitzpatrick (criador do Live Journal) e terminado recentemente Douglas Crockford. O artigo de Joel sobre Zawinski demonstra seu apreço pelo codificador pensante, ou aquele que faz as coisas acontecerem e não fica preso eternamente na armadilha da arquitetura. Eu acredito que as seguintes passagens do livro demonstram seu pensamento melhor do que se eu fosse tentar traduzi-los, começando por Jamie Zawinski:
Personally I have never believed that it is possible to be a good coder without being a good programmer nor a good programmer without being a good designer, communicator, and thinker. (...) Start converting it into the bad one until it stops working. That's primary tool of reverse engineering. (...) Your competitor's six-month 1.0 has crap code and they're going to have to rewrite it in two years but, guess what: they can rewrite it because you don't have a job anymore. (...) The design process is definitely an ongoing thing; you never know what the design is until the program is done. So I prefer to get my feet wet as early as possible; get something on the screen so I can look at it sideways.(...) I've noticed that one thing that separates good programmers from bad programmers is that good programmers are more facile at jumping between layers of abstraction they can keep the layers distinct while making changes and choose the right layer to make changes in. (...) I think one of the most important things, for me anyway, when building something from the ground up like that is, as quickly as possible, getting the program to a state that you, the programmer, can use it. Even a little bit. Because that tells you where to go next in a really visceral way. (...) I don't want to be a mathematician but I'm not going to criticize someone who is a mathematician. It's weird that people often confuse those two pursuits. People who are into very theoretical computer science are thought of in this same way as people who are shipping desktop applications. And they don't really have a lot to do with each other. (...) Then there was another book that everybody thought was the greatest thing ever in that same period'Design Patterns'which I just thought was crap. It was just like, programming via cut and paste. Rather than thinking through your task you looked through the recipe book and found something that maybe, kinda, sorta felt like it, and then just aped it. That's not programming; that's a coloring book. (...
De certa forma, o mesmo pragmatismo pode ser observado em Douglas Crockford, que utiliza o método de leitura de código tanto na entrevista por candidatos ("traga-me o código que tem orgulho de ter escrito e explique-o pra mim") quanto no dia-a-dia do projeto, para que todos entendam e aproveitem a evolução do projeto como um todo, além de constituir, na minha visão, uma das melhores dicas de auto-management que uma equipe de programadores poderia ter.
One of the things I've been pushing is code reading. I think that is the most useful thing that a community of programmers can do for each other'spend time on a regular basis reading each other's code. There's a tendency in project management just to let the programmers go off independently and then we have the big merge and then we have the big merge and if it builds then we ship it and we're done and we forget about it. One of the consequences of that is that if you have weak or confused programmers you're not aware of their actual situation until much too late. And so the risks to the project, that you're that you're going to have to build with stuff that's bad and the delays that that causes, that's unacceptable. The other thing is that you may have brilliant programmers on the project who are not adequately mentoring the other people on the team. Code reading solves both of those problems.
Can you talk a bit about how you conduct a code reading?
At each meeting, someone's responsible for reading their code, and they'll walk us through everything, and the rest of us will observe. It's a really good chance for the rest of the team to understand how their stuff is going to have to fit with that stuff.
We get everybody around the table; everybody gets a stack of paper. We also blow it up on the screen. And we all read through it together. And we're all commenting on the code as we go along. People say, 'I don't understand this comment,' or, 'This comment doesn't seem to describe the code.' That kind of stuff can be so valuable because as a programmer you stop reading your own comments and you're not aware that you're misdirecting the reader. Having the people you work with helping to keep your code clean is a huge service'you find defects that you never would've found on your own.
I think an hour of code reading is worth two weeks of QA. It's just a really effective way of removing errors. If you have someone who is strong reading, then the novices around them are going to learn a lot that they wouldn't be learning otherwise, and if you have a novice reading, he's going to get a lot of really good advice.
So if you don't clean up every seventh cycle you may be faced with the choice of whether or not to do a big rewrite. How do you know when, if ever, it's time for a big rewrite?
Generally the team knows when it's time. Management finds out a lot later. The team is getting beat up pretty regularly, making too many pretty regularly, making too many bugs; the code's too big, it's too slow; we're falling behind. They know why. It's not because they became stupider or lazier. It's because the code base is no longer serving the purpose that it needs to.
Esse pequeno trecho da entrevista de Brendan Eich, de Coders at Work, revela parte das frustações que os programadores de linha de frente sofrem com os ambientes de depuração, muitas vezes aquém dos desafios atuais. Sinceramente, não sinto isso em meu dia-a-dia, e acho o Visual Studio um excelente depurador com interface (mas que perde feio para o WinDbg em casos mais hardcore). Porém, fica a percepção curiosa do criador do JavaScript.
Proofs are hard. Most people are lazy. Larry Wall is right. Laziness should be a virtue. So that's why I prefer automation. Proofs are something that academics love and most programmers hate." - Brendan Eic
SGI:
Diagnosing it was hard because it was timing-sensitive. It had to do with these machines being abused by terminal concentrators. People were hooking up a bunch of PTYs to real terminals. Students in a lab or a bunch of people in a mining software company in Brisbane, Australia in this sort of '70s sea of cubes with a glass wall at '70s sea of cubes with a glass wall at the end, behind which was a bunch of machines including the SGI two-processor machine. That was hard and I'm glad we found it. These bugs generally don't linger for years but they are really hard to find. And you have to sort of suspend your life and think about them all the time and dream about them and so on. You end up doing very basic stuff, though. It's like a lot of other bugs. You end up bisecting'you know 'wolf fence.' You try to figure out by monitoring execution and the state of memory and try to bound the extent of the bug and control flow and data that can be addressed. If it's a wild pointer store then you're kinda screwed and you have to really start looking at harder-to-use tools, which have only come to the fore recently, thanks to those gigahertz processors, like Valgrind and Purify.
Ferramentas de Depuração Avançadas:
Instrumenting and having a checked model of the entire memory hierarchy is big. Robert O'Callahan, our big brain in New Zealand, did his own debugger based on the Valgrind framework, which efficiently logs every instruction so he can re-create the entire program state at any point. It's not just a time-traveling debugger. It's a full database so you see a data structure and there's a field with a scrogged value and you can say, 'Who wrote to that last?' and you get the full stack. You can reason from effects back to causes. Which is the whole game in debugging. So it's very slow. It's like a hundred times slower than real time, but there's hope.
Or you can use one of these faster recording VMs'they checkpoint only at system call and I/O boundaries. They can re-create corrupt program states at any boundary but to go in between those is harder. But if you use that you can probably close in quickly at near real time and then once you get to that stage you can transfer it into Rob's Chronomancer and run it much slower and get all the program states and find the bug.
Depuradores da Indústria:
Debugging technology has been sadly underresearched. That's another example where there's a big gulf between industry and academia: the academics are doing proofs, sometimes by hand, more and more mechanized thanks to the POPLmark challenge and things like that. But in the real world we're all in debuggers and they're pieces of shit from the '70s like GDB.
Yeah. So I use GDB, and I'm glad GDB, at least on the Mac, has a watch-point facility that mostly works. So I can watch an address and I can catch it changing from good bits to bad bits. That's pretty helpful. Otherwise I'm using printfs to bisect. Once I get close enough usually I can just try things inside GDB or use some amount of command scripting. But it's incredibly weak. The scripting language itself is weak. I think Van Jacobson added loops and I don't even know if those made it into the real GDB, past the FSF hall monitors.
Multithreading:
But there's so much more debugging can do for you and these attempts, like Chronomancer and Replay, are good. They certainly changed the game for me recently. But I don't know about multithreading. There's The multithreaded stuff, frankly, scares me because before I was married and had kids it took a lot of my life. And not everybody was ready to think about concurrency and all the possible combinations of orders that are out there for even small scenarios. Once you combine code with other people's code it just gets out of control. You can't possibly model the state space in your head. Most people aren't up to it. I could be like one of these chestthumpers on Slashdot'when I blogged about 'Threads suck' someone was saying, 'Oh he doesn't know anything. He's not a real man.' Come on, you idiot. I got a trip to New Zealand and Australia. I got some perks. But it was definitely painful and it takes too long. As Oscar Wilde said of socialism, 'It takes too many evenings.
E isso é tudo que guardarei deste livro. Talvez o revisite daqui a algumas décadas para comparar os novos tempos que viveremos.
In the real world one big split is between people who use symbolic debuggers and people who use print statements. - Peter Seibe
# Família Vende Tudo
Caloni, 2011-10-16 <cinema> <movies> [up] [copy]É fato que Lima Duarte está no estado de gênio, e cada novela que participa é um desperdício do Cinema. Semelhantes comparações podem ser feitas em boa parte do elenco de Família Vende Tudo, novo longa de Alain Fresnot. Este é um filme adiado em suas interpretações, por mais que não façam sentido ou soem deslocadas. E é aí que temos outro indício de desperdício, dessa vez no próprio Cinema: a capacidade de vender uma ideia divertida e fácil em uma história que sequer consegue chegar a uma conclusão sobre seu assunto central, e que desperdiça interpretações primorosas em um projeto sem pé nem cabeça.
O filme, em uma forte introdução de seus personagens, mostra a família-título em sua luta diária para sobreviver, comprando mercadorias no Paraguai e revendendo-as em São Paulo, ambas atividades ilegais e que acabam por deixar a situação financeira dessas pessoas, que já não era nada boa, uma calamidade, quando perdem tudo em uma barreira policial e em um arrastão da fiscalização.
Para tentar obter rapidamente o retorno do que foi perdido, o patriarca da familia (Duarte) tem uma ideia brilhante: fazer com que a filha engravide de um famoso cantor de música popular (Ciocler) e receba uma indenização por ter aliciado uma jovem "de menor". Detalhe que essa ideia foi inspirada em um dos testemunhos da igreja que seu filho frequenta (uma divertida participação de Marisa Orth).
Se, por um lado, mostrar a pobreza e a malandragem de uma família que tenta fazer de tudo para se dar bem rende boas e divertidas risadas (mais graças às interpretações do que às próprias piadas, que em geral soam de mal gosto e despropositadas), por outro lado não conseguir se firmar como comédia ou drama (ou até mesmo romance!?) durante o terceiro ato transforma a cambaleante experiência em um desastre total.
É uma pena, portanto, que Lima Duarte, Vera Holtz e tantos outros se vejam vendidos em um projeto como esse, que mais uma vez demonstra o despreparo de idealizadores influenciados muitas vezes pelas nossas famigeradas novelas em abordar temas tão sensíveis com tanto despudor.
# Qual Seu Número? (Mark Mylod, 2011)
Caloni, 2011-10-17 <cinema> <movies> [up] [copy]Aparentemente não há limites para a "criatividade" de Hollywood para comédias românticas. Quem diria que a Cindy (Anna Faris), da franquia Todo Mundo em Pânico, seria par romântico com o Capitão América (Chris Evans)? Um desafio interessante para ambos, visto que seus respectivos currículos de "menina fácil (e alvo de socos) em comédia-paródia" e "super-herói simpático" são ligeiramente diferentes nesse novo longa de Mark Mylod (Quem é Morto Sempre Aparece).
A história gira em torno da fascinação feminina pelas pesquisas de revistas femininas (nesse caso, a Marie Claire). Ally (Faris), durante os preparativos para o casamento de sua irmão Daisy (Graynor), percebe que o número de seus parceiros sexuais está ligeiramente acima da média nacional (o dobro) através de uma pesquisa da citada revista, e, de acordo com a mesma reportagem, mulheres que passam dos 20 parceiros acabam nunca se casando. Por coincidência, falta apenas um parceiro para que ela preencha os 20 redondos, e fatidicamente ela acaba preenchendo "a vaga" com quem não desejaria se casar. Desiludida, tem a "brilhante" ideia de reciclar seus ex-parceiros para conseguir não fugir às estatística da reportagem da revista feminina e evitar a maldição de ficar pra titia.
Essa proposta inicial (!?) é o que precisamos para dar início à caça de seus ex-namorados. Com potencial para ser divertido, soa bobo na maior parte das piadas, ainda mais quando percebemos cedo que a história já tem final definido, como quase sempre em comédias do gênero, mas que aqui infelizmente ainda nem a reviravolta gera o mínimo de tensão nos personagens.
Chris Evans, por sua vez, demonstra um apreço maior na simpatia de seu personagem, e é inevitável que ele ganhe carisma ao longo da trama, e esse inevitável é tanto por mérito de Evans quanto pela antipatia de Anna Faris, que parece mais determinada à comédia do que qualquer aspiração romântica que o filme possa ter.
Consciente da espécie de "road-movie metafórico" produzido, o diretor tenta escolher transições de planos que acabam chamando mais atenção para si mesmo que para o que está ocorrendo na tela. Pior ainda, porém, são as inconstantes câmeras tremidas, cujo motivo desconfio seja forçar a urgência nas ações de Ally, mas basta um momento de pausa para percebermos que não há motivo algum para tanta pressa assim da personagem.
Ciente da falta de emoção na maioria do longa, a trilha investe então na cena do casamento, apostando artificialmente em músicas românticas e consagradas em um volume nitidamente mais alto, tornando óbvio o desespero para que prestemos atenção ao destino de Ally (e é gritante a lição de moral "seja você mesma" jogada às pressas no terceiro ato, tanto que se aproveita da irmã, que até então era um simples adorno do roteiro, tanto que uma das músicas é de um cantor favorito de Ally).
Bobo e infantil do começo ao fim, ao menos possui coerência interna, e uma seleção de músicas simpática. Mas é só.
# Depuração de emergência: receita de bolo
Caloni, 2011-10-18 <computer> [up] [copy]Continuando o papo sobre o que fazer para analisar rapidamente um crash no servidor com o pacote WinDbg, na maioria das vezes a exceção lançada pelo processo está diretamente relacionada com um acesso indevido à memória, o que tem diversas vantagens sobre problemas mais complexos:
* Possui localização precisa de onde ocorreu a violação (inclusive com nome do arquivo-fonte e linha).
* Não corrompe a pilha (ou, se corrompe, não chega a afetá-la a ponto da thread ficar irreconhecível).
* A thread que contém a janela de crash é a culpada imediata (basta olha a pilha!).
Bom, resumindo: basta olhar a pilha! Mas, para isso ser efetivo, precisaremos do PDB do executável que gerou o crash, pois através dele é possível puxar a tal localização da violação de acesso.
Se você mantiver executável (DLL também é executável) juntinho com seu PDB, sua vida será mais fácil e florida.
Mesmo que, em alguns momentos trágicos, apareça uma tela indesejada.
Seu caminho a partir dessa tela pode ser analisar um dump gerado (visto no artigo anterior) ou podemos atachar o WinDbg diretamente no processo (visto aqui e agora):
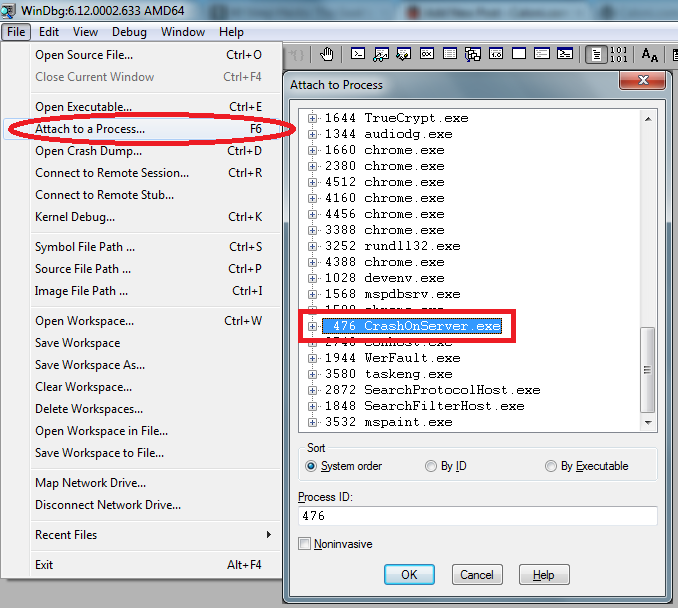
WinDbg: "mas que bagunça é essa na memória desse processo?"
O comando mais útil na maioria dos casos é mostrar a pilha em modo verbose (kv e enter). Porém, antes disso, precisamos:
1. Ajeitar o path dos símbolos.
2. Recarregar o PDB do executável suspeito.
3. Mostrar a pilha de todas as threads (até descobrir a culpada).
Todos esses comandos podem ser vistos abaixo. São, respectivamente, .symfix, .reload e novamente o kv (mas para todas threads).
0:001> .symfix
0:001> .reload /f CrashOnServer.exe
*** WARNING: Unable to verify checksum for C:\Users\wanderley.caloni\Documents\Projetos\Caloni\Posts\Debug\CrashOnServer.exe
0:001> kv
Child-SP RetAddr : Args to Child : Call Site
0030f918 77679198 : 00000000`00000000 `00000000 : ntdll!DbgBreakPoint
0030f920 775e244d : 00000000`00000000 `00000000 : ntdll!DbgUiRemoteBreakin+0x38
0030f950 00000000 : 00000000`00000000 `00000000 : ntdll!RtlUserThreadStart+0x25
0:001> ~* kv
0 Id: 1dc.978 Suspend: 1 Teb: 00000000`7efdb000 Unfrozen
Child-SP RetAddr : Args to Child : Call Site
0008ea48 751f282c : 00000000`77770190 00000000`001dfb50 : wow64cpu!CpupSyscallStub+0x9
0008ea50 7526d07e : 00000000`00000000 00000000`775b3501 : wow64cpu!WaitForMultipleObjects32+0x32
0008eb10 7526c549 : 00000000`00000000 00000000`7ffe0030 : wow64!RunCpuSimulation+0xa
0008eb60 775cae27 : 00000000`003b3710 00000000`7efdf000 : wow64!Wow64LdrpInitialize+0x429
0008f0b0 775c72f8 : 00000000`00000000 00000000`00000000 : ntdll!LdrpInitializeProcess+0x1780
0008f5b0 775b2ace : 00000000`0008f670 00000000`00000000 : ntdll! ?? ::FNODOBFM::`string'+0x2af20
0008f620 00000000 : 00000000`00000000 00000000`00000000 : ntdll!LdrInitializeThunk+0xe
Ops! Estamos rodando um processo 32 dentro de um SO 64 (Windows 7, por exemplo). Isso pode acontecer. Seguimos com o workaround .load wow64exts e .effmach x86:
0:001> .load wow64exts
0:001> .effmach x86
Effective machine: x86 compatible (x86)
0:001:x86> ~* kv
0 Id: 1dc.978 Suspend: 1 Teb: 7efdb000 Unfrozen
ChildEBP RetAddr Args to Child
001df24c 761a0bdd 00000002 001df29c 00000001 ntdll_77760000!NtWaitForMultipleObjects+0x15 (FPO: [5,0,0])
001df2e8 7727162d 001df29c 001df310 00000000 KERNELBASE!WaitForMultipleObjectsEx+0x100 (FPO: [Non-Fpo])
001df330 77271921 00000002 7efde000 00000000 KERNEL32!WaitForMultipleObjectsExImplementation+0xe0 (FPO: [Non-Fpo])
001df34c 77299b2d 00000002 001df380 00000000 KERNEL32!WaitForMultipleObjects+0x18 (FPO: [Non-Fpo])
001df3b8 77299bca 001df498 00000001 00000001 KERNEL32!WerpReportFaultInternal+0x186 (FPO: [Non-Fpo])
001df3cc 772998f8 001df498 00000001 001df468 KERNEL32!WerpReportFault+0x70 (FPO: [Non-Fpo])
001df3dc 77299875 001df498 00000001 38239b1e KERNEL32!BasepReportFault+0x20 (FPO: [Non-Fpo])
001df468 777d0df7 00000000 777d0cd4 00000000 KERNEL32!UnhandledExceptionFilter+0x1af (FPO: [Non-Fpo])
001df470 777d0cd4 00000000 001dfb34 7778c550 ntdll_77760000!__RtlUserThreadStart+0x62 (FPO: [SEH])
001df484 777d0b71 00000000 00000000 00000000 ntdll_77760000!_EH4_CallFilterFunc+0x12 (FPO: [Uses EBP] [0,0,4])
001df4ac 777a6ac9 fffffffe 001dfb24 001df5e8 ntdll_77760000!_except_handler4+0x8e (FPO: [Non-Fpo])
001df4d0 777a6a9b 001df598 001dfb24 001df5e8 ntdll_77760000!ExecuteHandler2+0x26
001df580 7777010f 001df598 001df5e8 001df598 ntdll_77760000!ExecuteHandler+0x24
001df584 001df598 001df5e8 001df598 001df5e8 ntdll_77760000!KiUserExceptionDispatcher+0xf (FPO: [2,0,0])
WARNING: Frame IP not in any known module. Following frames may be wrong.
001df9ac 010d141e 00000000 00000000 00000000 0x1df598
001dfa90 010d19af 00000001 00321410 00321c70 CrashOnServer!main+0x2e (FPO: [Non-Fpo]) (CONV: cdecl)
[c:\users\wanderley.caloni\documents\projetos\caloni\posts\crashonserver\crashonserver.cpp @ 13]
001dfae0 010d17df 001dfaf4 77273677 7efde000 CrashOnServer!__tmainCRTStartup+0x1bf (FPO: [Non-Fpo]) (CONV: cdecl)
[f:\dd\vctools\crt_bld\self_x86\crt\src\crtexe.c @ 555]
001dfae8 77273677 7efde000 001dfb34 77799f02 CrashOnServer!mainCRTStartup+0xf (FPO: [Non-Fpo]) (CONV: cdecl)
[f:\dd\vctools\crt_bld\self_x86\crt\src\crtexe.c @ 371]
001dfaf4 77799f02 7efde000 6b3e1b48 00000000 KERNEL32!BaseThreadInitThunk+0xe (FPO: [Non-Fpo])
001dfb34 77799ed5 010d1109 7efde000 00000000 ntdll_77760000!__RtlUserThreadStart+0x70 (FPO: [Non-Fpo])
001dfb4c 00000000 010d1109 7efde000 00000000 ntdll_77760000!_RtlUserThreadStart+0x1b (FPO: [Non-Fpo])
# 1 Id: 1dc.1b0 Suspend: 1 Teb: 7efd8000 Unfrozen
ChildEBP RetAddr Args to Child
0056ffe8 00000000 00000000 00000000 00000000 ntdll_77760000!RtlUserThreadStart (FPO: [0,2,0])
Nosso depurador favorito acusa uma pilha que contém a função WerpReportFault (Web Error Report, mas qualquer outra função com Exception no meio seria uma candidata). E, nessa mesma thread, a última linha nossa conhecida está no arquivo crashonserver.cpp:13. Isso nos revela o seguinte:
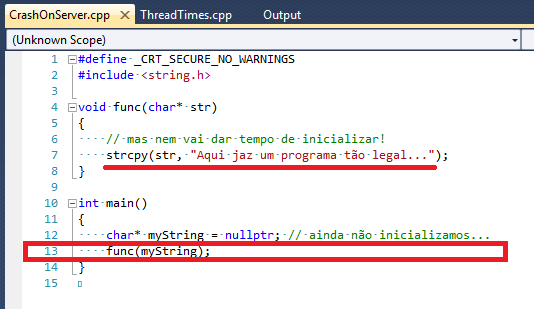
E essa situação, caro leitor, é 10% de tudo o que você precisa saber sobre WinDbg para resolver, mas que já resolve 90% dos casos. Belo custo-benefício, não?
# Trabalhar Cansa (Juliana Rojas, 2011)
Caloni, 2011-10-18 <cinema> <movies> [up] [copy]Esse drama-terror concebido e dirigido por Juliana Rojas e Marco Dutra (esse, um dos roteiristas do recente Meu País) busca evitar se posicionar claramente no sobrenatural, mas dá uma gélida impressão durante toda a trama que é exatamente com isso que estamos lidando, ainda que não seja dito ou declarado. E é esse o detalhe mais aterrorizante de todo o longa.
Concebida sua introdução em moldes tradicionais -- como pode-se notar nos detalhes triviais de uma casa ou até mesmo do armazém recém-inaugurado -- o filme conta a história de Helena (Albergaria), Otávio (Descartes) e da pequena Vanessa, uma família que passa por apuros financeiros decorrentes da recente demissão do pai, e que tem a partir daí a figura da mãe como predominante, pois esta pretende abrir um armazém de bairro em um local antes abandonado pelos antigos comerciantes.
Desenvolvendo a trama da forma mais natural possível -- com trilha sonora inexistente -- aos poucos vamos percebendo a dinâmica marido-esposa e a determinação cada vez mais perniciosa de Helena em conseguir com que o armazém vá pra frente, enquanto assistimos ao declínio de Otávio, com sérias dificuldades de conseguir um novo emprego, aguçados ainda mais pela sua idade já avançada.
Esses detalhes que delineiam as relações entre os personagens são os mesmos usados para nos fazer crer que algo oculto impede que Helena tenha sucesso em sua empreitada. Detalhes sutis chegam a evocar o sobrenatural, embora muito mais de uma forma metafórica ou até mesmo cultural, muito presente no uso dos sons, nas sombras e principalmente na câmera, que consegue arrumar um jeito em que até simples pegadas no chão são capazes de nos manter presos na poltrona com a respiração suspensa.
Porém, o astucioso roteiro não se entrega ao óbvio, nem que ele esteja tão próximo. Prefere dar esse gostinho ao espectador, que vai mastigando aos poucos, na imaginação, as lacunas que parecem faltar. Para alguns, parecerá simplista demais (ainda que irresistível de acompanhar). Para outros, um exercício estético e interativo tão delicioso quanto o que temos em A Bruxa de Blair, embora este mais refinado, nas entrelinhas.
A participação inspirada e apática de Helena comprova nossos pensamentos mais maldosos a respeito do destino do mercado, enquanto o declínio paulatino de Otávio passa quase despercebido, mas equilibra a história sobre dois pontos de vista: o mal crescente e o enfraquecimento do bem. Nós mesmo exercitaremos essa ambiguidade em muitos eventos. Quando o cachorro aparece a latir, por exemplo, se em um primeiro momento enxergamos o acaso do cotidiano, a montagem no ritmo certo nos permite chegar a outra conclusão, mais nefasta, o que vai se tornando mais comum até prevalecer completamente sobre o senso comum (em uma bela rima do que vai acontecendo no próprio filme).
# Despedida em Las Vegas (Mike Figgis, 1995)
Caloni, 2011-10-22 <cinema> <movies> [up] [copy]Talvez eu seja vítima da regra dos 15 anos -- a que reza que qualquer filme visto antes dos 15 anos continua em nossa memória como bom -- mas Ben e Sera foram dois dos personagens mais queridos da minha juventude de cinéfilo. Adorava a entrega completa de Nicholas Cage e de Elizabech Shue em seus papéis que ainda considero os melhores de ambos, em um filme deprimente do começo ao fim. Essa minha revisita continua a confirmar o fato de que, se Cage costuma ser criticado por overacting, aqui praticamente esquecemos que existe algum ator por trás do divertido, patético e trágico Ben Sanderson.
Mas, agora, lembrando, vejo que talvez não tivesse sido uma boa ideia ver um filme desses antes dos 15 anos.
A história não poderia ser mais simples: Ben (Cage) é um roteirista que, vítima da bebida, se torna um alcoólatra inveterado e acaba perdendo o emprego. Decide então, largar tudo e se embebedar em Las Vegas até a morte. O passado de Ben é mencionado brevemente através de uma foto com mulher e filho, foto essa que queima em uma pilha de pertences que ele deixa para trás rumo ao seu suicídio etílico. Tudo o que temos é a impressão do próprio Ben: que em algum momento desconhecido de seu passado ele tinha uma vida feliz e normal.
Sera (Shue), por sua vez, é uma prostituta que veio com seu cafetão de um país do Leste Europeu e que mantém com ele uma relação doentia, ao ponto de sofrer humilhações e agressões. Exatamente pela única pessoa com quem poderia ter um contato afetivo ser um anormal é com que faz com que Sera sinta-se cada vez mais só e desamparada, e é admirável constatar que Elizabeth Shue desempenhe tão bem as funções de prostituta em Las Vegas e companheira de Ben/Cage em seus últimos dias.
Aliás, para o bom funcionamento do filme, foi vital que o encontro entre os dois fornecesse essa química que percebemos desde o primeiro diálogo próximo entre eles, para entendermos quais as razões de ambos para estarem juntos. Mais importante ainda, é constatar que este não é um conto de fadas, e ambos têm consciência de seus atos. Às vezes imagino o filme sem as participações de Sera em uma espécie de analista, em que ela abre seus sentimentos em relação a Ben, mas considero hoje uma função não-descartável da narrativa pelo fato dela, apesar de prostituta, ser extremamente tímida (mais uma complexidade digna de aplausos na constituição do personagem de Shue, que não se entregou ao estereótipo fácil e tão comum no Cinema e na vida).
Ben, ao contrário, é um ser totalmente exposto, exposição essa que por conta da bebida chega a torná-lo até patético em muitos momentos, mas em nenhum deles ele perde a empatia do espectador, fazendo algo desagradável ou repugnante (o que demonstra não só a entrega de Cage ao papel, como o total controle que este tem em seu personagem). Seu andar cambaleante e sua cabeça cabisbaixa pode até soar estereotipado, mas a forma de fazer graça e adicção de sua fala são tão expressivas que sequer notamos estar diante de um bêbado típico.
O clima depressivo do filme é ajustado (leia-se aumentado) através de uma seleção inspiradíssima de músicas que evocam ritmos mais lentos e reflexivos (aliás o próprio diretor e Cage participam na confecção de algumas trilhas). Os ângulos da câmera e a fotografia distorcida gera tanto a sensação que a bebida causa em Ben quanto a concepção artística de Las Vegas como uma cidade que vive de dejetos humanos e de falsidades. A relação de ambos com as outras pessoas também é sempre baseada nessas assumpções, o que reforça mais ainda o sentimento de excluídos e às margens da sociedade).
É trivial falar que ambos os atores fizeram sua lição de casa para viveram personagens tão marcantes, chegando Cage a frequentar o "AA" e Shue a ter conversas de campo com garotas de programa. Porém, ainda sou levado a acreditar naqueles casos de filmes que são feitos no lugar certo pelas pessoas certas. O resultado nesse caso não poderia ter sido melhor.
# Vida e Software
Caloni, 2011-10-22 [up] [copy]Desenvolver software está bem longe de ser uma ciência exata e muito próxima de ser uma ciência humana. Eu, pessoalmente, considero um ramo esotérico, onde vale muito mais ter a atitude de reconhecer que não temos muito controle sobre como as coisas funcionam do que querer ter as rédeas de algo desgovernado.
Não sei bem o motivo. Talvez por existirem muitas camadas o software não consegue ser normalizado como as propriedades físicas dos blocos que montam um prédio ou um transatlântico. Ou simplesmente existem variáveis demais na própria camada da aplicação que impedem a compreensão total do problema (como sabemos se estamos dentro da Matrix? Como o software sabe se está em um ambiente virtualizado?).
Para os piores casos, o software sempre vai ter que confiar em seu ambiente e as regras, aparentemente imutáveis, que o regem. Ele precisar confiar não o exime de controlar seus próprio limites, e é aí que recai a atitude do programador, atitude essa que reflete diretamente nossa visão sobre a vida.
Já vi muitos programadores (eu me incluo) deixando o código pronto para o melhor dos mundos e dando a tarefa por concluída. Otimismo demais? Desleixo? Ou arrogância? Qualquer que seja o motivo, ele está incrustado na própria visão de vida do programador e de como ele se vê no mundo. Eu, particularmente, fico horrorizado com código assim. Não com todos, mas com os que são visivelmente importantes e que necessitam de um carinho especial. São os alicerces para outros códigos, de repente.
Outra atitude igualmente deformada é achar que o mundo vai acabar se não existirem todos os sanity checks (até os mais bizarros) em qualquer meia-dúzia de linhas. É o paranóico, que pode se dar bem no tipo de código importante já citado, mas que nunca vai conseguir entregar um projeto trivial se for baseado em libs escritas pelos outros e cujo código nunca deu uma "lida rápida". Aliás, essa mesma atitude "deu uma lida" demonstra que o pessimista pode ser ainda mais arrogante, pois acredita conseguir capturar toda a complexidade do sistema apenas lendo seu código en passant.
De uma forma ou de outra, como toda atividade humana, escrever código nos define não apenas como bons programadores, mas como bons humanos, com seu conjunto de crenças e valores. O que, de certa forma, é um bom sinal, pois melhorando como seres humanos, melhoramos como programadores. E vice-versa.
- Para quê filosofia?, por Marilena Chauí.
# O Manuscrito Perdido (José Barahona, 2010)
Caloni, 2011-10-23 <cinema> <movies> [up] [copy]Fradique Mendes, um poeta e aventureiro português, amigo de Eça de Queiroz, viveu na região que foi primeiro abordada pelos portugueses no começo do século XVI, evento esse que nós brasileiros conhecemos como "Descobrimento do Brasil". Esse evento, e muitos outros na história do país, no entanto, possuem ecos diversos na sociedade brasileira, como bem demonstra esse documentário de José Barahona. O mais relevante desse trabalho, porém, é constatar que esses ecos do passado continuam influenciando boa parte da nossa sociedade, e como ela é estruturada em torno da terra herdada.
O objetivo de Barahona é resgatar um suposto manuscrito escrito por Fradique ao deixar suas terras. Vítima de ódio de outros proprietários depois que este decide libertar seus escravos, o manuscrito é resultado de reflexões do poeta acerca da sociedade onde vivia.
Apesar da qualidade das imagens capturadas deixar a desejar (ou foi a projeção tosca, mesmo?) e até mesmo o foco nos entrevistados apresentar problemas sérios nos primeiros momentos, a decupagem merece destaque, pois possui uma lógica visual competente, mesmo ao sabermos que diversos pontos da trama foram "costurados" com a ajuda de atores.
Através de uma narração em off, somos levados a crer que o documentarista está sozinho nessa empreitada, e o fato da maioria das tomadas ser gravada com a câmera em tripé reforça essa impressão. Porém, mais isolado que o cineasta estão as comunidades que ele visita, que parecem alheias a tudo que ocorre no mundo, com as pessoas vivendo em seus microcosmos resultantes de mudanças sociais de séculos atrás.
Dessa forma, acompanhamos descendentes das tribos quilombolas, os primeiros escravos refugiados, assim como as tribos indígenas que, diferente da Amazônia, por estarem situados na costa do continente, sofreram influência direta por 500 anos.
E para terminar o caldo, indígenas e sem-terra disputam a posse de terras na mesma região, em um triste reflexo do que era naqueles tempos primitivos e que vem se repetindo de geração em geração, em um povo que pode carecer de muitos lazeres da vida moderna, mas que nunca deveria sentir falta do bem mais abundante no país: a própria terra.
# Roubando Vidas (D. J. Caruso, 2004)
Caloni, 2011-10-23 <cinema> <movies> [up] [copy]Esse é mais um thriller policial que envolve uma dupla de elementos que vem se tornando frequente: histórias previsíveis e Angelina Jolie. Nesse caso, Jolie é uma agente do FBI que precisa capturar um serial killer que rouba a identidade de suas vítimas.
A trama principal, por se revelar boba e previsível desde seu início, se torna enfadonha, pois já sabemos seu desenrolar, o que se torna simples uma vez que o filme joga com todas as cartas marcadas, chegando a aplicar o velho clichê dos gêmeos de temperamentos diversos.
(É sempre bom repetir, nada tenho contra clichês bem usados, mas note a montagem dos diálogos da mãe de um dos suspeitos e perceberá parte do maniqueísmo empregado por todo o filme para enganar os espectadores mais desavisados.)
Mesmo assim, o clima sombrio em que é transformada a cidade onde os crimes ocorrem, captada pelas eficientes lentes de Amir Mokri balanceiam a falta de personalidade da trilha sonora, que oscila entre noir e drama psicológico, sem nunca agradar em nenhum dos subgêneros.
E por falar em psicologia, talvez o maior erro do filme tenha sido apostar na performance mental do serial killer, o que, infelizmente nesse caso, ainda mais depois do desfecho, revela um conceito que parece ainda inacabado e que aplica subterfúgios pedestres para que pareça mais complexa do que de fato é. Não há detalhes que eu possa revelar sem deixar a história mais previsível ainda, portanto, me abstenho.
Ao final, pelo menos ficamos com os olhos e os lábios de Angelina Jolie, o que é sempre um atrativo, não importando muito o gênero do filme ou sua história.
# A Morte de Pinochet (Bettina Perut, Iván Osnovikoff, 2011)
Caloni, 2011-10-24 <cinema> <movies> [up] [copy]O superzoom inicial das rugas (passado) e dos lábios (testemunho) das pessoas entrevistadas no documentário sobre o ditador sanguinário possuem dois motivos igualmente inteligentes e controversos: primeiro, impede que olhemos diretamente para os que dizem ter um profundo sentimento de admiração e orgulho por um ser responsável por uma das ditaduras mais cruéis que já se ouviu falar, o que evita nossa repulsa imediata por essa gente; segundo, admite que o testemunho dessas pessoas é fiel e honesto, dito diretamente de suas bocas, que muitas vezes sofreram inconscientemente os infortúnios de um regime que, para elas, não tem qualquer relação com o amado general.
Já, ao enfocar os cidadãos que festejam alegremente em Santiago, a capital do país, após a declaração de morte do ex-ditador, há uma inversão na estrutura, e agora, sim, fazemos parte daquele grupo que festeja e se revolta por ele nunca ter sido julgado pelos crimes que cometeu. É o segundo lado humano retratado no longa.
A forma de conciliar ambas as visões do regime ditatorial do Chile é o segredo para que entendamos como é possível que um governo como aquele conseguiu ficar tanto tempo no poder. Oras, se há parte significativa do povo que o apóia, independente de seus brutais métodos, e que até o compara (de maneira orgulhosa) ao próprio Hitler, então não há dúvida que Pinochet pode ser o ícone desse regime, mas nunca esteve sozinho.
Para os brasileiros que venham a assistir o depoimento dos fãs de Pinochet, vale a fala de uma jovem, tão repetida em nossa própria terra, defendendo de forma completamente alheia à realidade que "na época da ditadura as coisas eram melhores". Sim, é capaz, também, que seja um depoimento sincero. E exatamente por causa disso é que o filme carrega um peso moral imensurável ao estabelecer como pessoas obviamente idôneas e sinceras venham a apoiar algo completamente errado sob a ótica humanista.
O momento mais icônico, onde o filme se encontra, é quando uma das fãs do ditador se revolta após descobrir que após a sua morte sua licença para trabalhar como comerciante fora cassada. Alegando ser esse o sustento de sua família, brada em frente à camera, exigindo seus direitos e se perguntando onde estão os direitos humanos.
Pois é. A realidade, de fato, muitas vezes está nos olhos do que apenas queremos ver.
# Aleksander Sokurov: Uma Questão de Cinema (Aleksandr Sokurov, 2011)
Caloni, 2011-10-24 <cinema> <movies> [up] [copy]Quando o diretor de Arca Russa tem algo a falar sobre movimento e sonoridade no cinema, ou da própria questão do cinema em si, deve haver algo de importante, ou até mesmo essencial, para se captar. No entanto, Alexandre Sokurov (ou a montagem de Anne Gigleux) não é exatamente didática. É necessário, assim como o trabalho do próprio diretor-tema, sentir a ação antes dela acontecer. O resultado, como um todo, é no mínimo inspirador.
Autor de inúmeros curtas e longas, incluindo diversos documentários e já citada Arca Russa, um filme de 91 minutos gravado em uma única sequência dentro do Museu Hermitage, Sokurov aparentemente encara o aspecto psicológico da ação como a própria ação, o que explicaria as cenas inertes que são usadas como exemplos de sua cinegrafia e que ilustram seu ponto de vista no decorrer de seu discurso.
A primeira impressão ao acompanhar seu monólogo é uma sopa de conceitos que vai e vem e chega a apresentar um tédio terrível, que vai se apoderando do espectador em seus exaustivos 61 minutos. Porém, a boa notícia é que o conjunto da experiência é satisfatória como reaprendizado do que é Cinema sob a ótica de um diretor consagrado, que sequer considera a sétima arte uma arte de fato, por não possibilitar o "controle absoluto" do artista.
Esse controle que ele se refere, porém, consegue ser visto na maioria dos seus exemplos, com o uso de luz, câmera e efeitos sonoros. Muito do que é visto se mistura com as divagações do diretor, mas o exemplo mais completo, ou pelo menos central no debate sobre a família e o povo russo, é um quadro lentíssimo em que vemos um trem se aproximar e percorrer todo o horizonte enquanto um garoto observa logo à frente. Se o acompanhamento do espectador desse quadro não é o controle absoluto que Sokurov desmente, não sei mais o que é.
# Nervos à Flor da Pele
Caloni, 2011-10-24 <cinema> <movies> [up] [copy]Da minha limitada (põe limitada nisso) experiência, o que já vi do cinema islandês é que ele foca muito na relação e nas descobertas dos seus jovens, e este, acredite, não foge nem um pouco da fórmula. Apresentando desde o início a descoberta de um jovem de ser gay, esse pequeno segredo dele permeia todo o longa, servindo de contraponto com a relação dos outros personagens e seus anseios. Por exemplo, a melhor amiga desse jovem, encontra suporte em seu jeito doce, mas, equivocada, não sabe se está afim dele ou não.
De maneira semelhante, vemos festas da adolescência salpicadas com esse tipo de relacionamento, até que somos levados a uma conclusão trágica de uma das personagens, mas que nem de longe chega a ser o "Nervo à Flor da Pele" do equivocado título em português. Na verdade, o filme segue um ritmo bem leve para chegarmos a pensar que possui alguma pretensão dramática acima do exposto.
# O Desaparecimento do Gato (Carlos Sorín, 2011)
Caloni, 2011-10-24 <cinema> <movies> [up] [copy]Diferente da ótica tão comum nos filmes de encarar a loucura como uma doença trágica, Carlos Sorín dedica seus esforços em sua nova película para entreter o espectador e deixá-lo ver com seus próprios olhos que a loucura, de uma maneira geral, pode estar em todos nós, da maneira mais corriqueira e cotidiana que for. De maneira brilhante, O Desaparecimento do Gato consegue transmitir essa sensação através de inúmeras facetas.
A história começa com o relatório médico de três especialistas que decidem que um de seus pacientes está curado, e que portanto está livre para voltar à sua vida normal do lado da esposa. No entanto, esta, por ter vivenciado seu ataque de loucura, não está tão certa ainda da sanidade de seu marido, e embora tente de tudo para voltar à normalidade, acaba sempre voltando para a mesma questão que a remoe por dentro: estará seu marido verdadeiramente curado de uma doença mental?
De forma quase que metafórica, o gato da família é usado como estopim para suas suspeitas, pois assim que seu marido chega ele some de casa e nunca mais aparece. Aliás, a piada recorrente da mulher colocando comida à noite para ele é eficiente em todas as vezes, pois Sorin entende que o próprio espectador aguarda com certa ansiedade a resolução do "caso".
Mais interessante, no entanto, é que aos poucos somos levados a crer que tudo o que acontece na vida do casal é, de certa forma, normal na vida de qualquer pessoa, e muitas das esquisitices de Luis (Luque) nós mesmos muitas vezes já nos pegamos na mesma situação. Aliás, Luis Luque é eficiente ao máximo ao deixar essa faceta de sua personalidade oscilando, de forma que sempre nos acalmamos com sua face inocente (mas sempre com um pé atrás). Norma Argentina, como sua esposa Ángela, dá um banho nas expressões e no modo de agir preocupada, criando um equilíbrio quase imperceptível entre os dois personagens.
Porém, e aí entra a genialidade de Sorín, essa "vida normal" que vemos é exposta através de uma lente que insiste em olhar as coisas de ângulos diferentes, onde até ouvir uma pessoa cantando pode despertar um sintoma preocupante (e a transição de uma trilha sonora de suspense para o sinal de um telefone é surpreendentemente funcional). Outro ponto são os closes um pouco acima do normal das faces dos personagens, o que evoca o ponto de vista de cada um sobre o que vai acontecendo (ao mesmo tempo que deixa todo o resto meio desfocado, em uma alusão ao mundinho privado em que os loucos vivem).
E diferente de um filme recente que vi (o péssimo Roubando Vidas), onde o óbvio chega a ser uma ofensa ao espectador, nesse caso sabemos que muitos elementos do longa são previsíveis, mas entramos de tal forma na atmosfera paranoica da esposa que um simples saco de lixo pode se transformar de uma hora pra outra em algo mais. Isso funciona tão bem porque, assim como ela, nós também temos nossas dúvidas sobre a sanidade de Luis.
Mantendo o controle absoluto da história, a conclusão tensa enriquece novamente toda a experiência, pois detalhes menos importantes passam a corresponder ao nosso entendimento (como as férias para o Brasil). E isso faz toda a diferença em uma história de qualidade.
# As Flores de Kirkuk
Caloni, 2011-10-25 <cinema> <movies> [up] [copy]A aparente originalidade desse filme situado na história do Iraque sob o comando do ditador Saddam Hussein, que promoveu uma matança de povos que não apoiavam seu regime, reside no seu diretor italiano e em sua estrutura formulaica, que lembra romances novelescos, mas que aparece erroneamente embutido em uma atmosfera de drama e desolação.
O núcleo da história gira em torno do amor incondicional entre Najla (Alaoui), de uma família influente e fiel a Saddam, e Sherko (Eser), um médico descendente de curdos, um povo inimigo do ditador. Fornecendo uma introdução que parte direto para um flashback gigante, que se torna a história contada no filme, os momentos de romance do casal contam com diálogos extremamente piegas e vexatórios, sem contar na interpretação novelesca do casal, que passa a sensação de ter sido construído com essa intenção.
Para reforçar essa impressão, as cenas da primeira parte são montadas de acordo com uma narrativa teatral, com a câmera em mãos, sempre enquadrando o cenário como se fosse um palco (ou seja, o movimento dos atores quase sempre ocorre em apenas um quadro). As próprias falas já citadas também corroboram essa teoria, principalmente as da protagonista com seu amante, que soam desnecessariamente clichês e quase surreais se contextualizadas com o clima de conflitos internos que o povo vive. E o que falar do vilão canastrão, que deseja se casar com ela, possui posição de status e mesmo assim nunca consegue fazê-la sentir medo (nem a nós)?
Talvez a intenção original tenha sido mesmo tornar o filme uma espécie de conto de fadas, pois a própria fotografia aparece muito mais colorida do que deveria em um território desértico (e, portanto, inóspito). Porém, a tentativa de soar como fuga da realidade não esconde a maior falha do longa, que é nunca se localizar em um gênero principal que o defina, o que termina por enfraquecer ambas as histórias, que soam independentes e nunca transitam organicamente: o massacre histórico ocorrido no país e o romance cafona do casal de namorados.
# Là-bas: Educação Criminal
Caloni, 2011-10-25 <cinema> <movies> [up] [copy]Um filme não necessariamente precisa ter um excelente roteiro para levar o espectador a pensar muito a respeito. Algumas vezes, bastam pequenos detalhes que levem em consideração: 1) a inteligência de quem assiste e 2) a motivação narrativa por trás da informação, que o filme fluirá e trará algo de novo para a gaveta de conhecimentos do cinéfilo.
Esse parece ser o caso desse La Bàs: Educação Criminal, que pelo próprio título já sugere algum tipo de ação ilegal na história. De fato, somos apresentados logo no início a um texto que explica que os africanos imigrados na Itália são proibidos por lei de terem um emprego. Isso já faz pensar de imediato o que essas pessoas fazem para ganhar a vida, e é assim que o fio do enredo se inicia.
Usando de uma fotografia cinzenta, triste e empoeirada, dando ao mesmo tempo as sensações de isolamento e de tristeza, logo no começo somos apresentados a um elemento que foge desse padrão: um guarda-chuva vermelho. O vermelho, aqui, representa o usual: perigo, crime, sangue. Com o seu uso estimulado em diversas tomadas, logo aprendemos a observar como as cores se relacionam em diversos planos, e logo notamos que o vermelho exerce uma função narrativa que não pode ser ignorada.
Da mesma forma a bebida. O protagonista, muçulmano, está proibido de beber pelas leis de sua religião. De qualquer forma, ele bebe eventualmente; e esse é o detalhe sublime: sempre acompanhado de uma mulher. Mulheres e bebidas são associados dessa forma, simples, direta e nada sutil.
Ao falar de racismo no filme, nada mais irônico do que colocar capuzes brancos na gangue de africanos que comanda o tráfico de drogas da região, liderados pelo tio do protagonista. Mais ironicamente ainda, a gangue rival, formada por brancos, se veste de preto em seus ataques.
No final, toda essa simbologia de cores se esvai em um terno branco esquecido na floresta. Representando a subida de status do nosso herói, agora representa sua liberdade, e por consequência sua salvação. O protagonista renasce, como veio ao mundo e como é visto pelo filme como símbolo de pureza: negro.
# Laços Humanos
Caloni, 2011-10-27 <cinema> <movies> [up] [copy]É até sacanagem querer escrever um pouco sobre Laços Humanos, trabalho impecável de Elia Kazan (que, acabei de descobrir, é seu primeiro longa!). De certa forma, não parece correto apontar virtudes técnicas em um filme que fale direto com o coração. Não é raro para mim assistir filmes que me faça lacrimejar compulsivamente uma ou duas vezes durante a sessão, mas nesse caso o filme inteiro tem algo de mágico e esperançoso, que deixa o espectador com o coração apertado boa parte do tempo.
Só que as coisas não são tão simples. Ao mesmo tempo que transborda esperança e sonhos no aspecto de alguns personagens, o filme consegue atingir de maneira muito mais sutil a crueldade, o realismo e muitas vezes a ironia na mesma cena. Tudo isso fruto talvez da visão de Kazan (ajudado pelo excelente roteiro da dupla Tess Slesinger e Frank Davis), que pode ser acusado de pessimista, mas nunca de ter feito um filme sem emoções.
Essas não faltam. Seus personagens são exacerbados. A filha é doce demais, e a interpretação da atriz a faz parecer um anjo que caiu do céu. Só que por ser dessa forma torna mais evidente que ela representa nós mesmos e nosso otimismo exagerado na vida (assim como seu pai). Por outro lado, um triste lado, da mesma forma também nos vemos refletidos na mãe (e quem nunca zombou dos sonhos dos outros, ou acordou as pessoas para a "dura realidade da vida"?). Em escala menor, temos sua irmã e o policial como guias morais, ambos também presentes nessa complexa formação que é o ser humano. Tudo reflete no espectador, que acompanha entorpecido os diálogos lindos, mas utópicos, de um lado, mas concorda com a visão sensata, ainda que dura (e muitas vezes cruel), de outro. Todo esse caldeirão de emoções é cozinhado de maneira que possamos sentir todos os aspectos emocionais ao mesmo tempo, o que nos ajuda a entender a função primordial de cada personagem e, em uma camada psicológica, a função de cada emoção refletida em nós mesmos.
E para "mexer bem esse caldeirão" a direção consciente de Kazan busca unir os quadros da forma mais arrastada possível, com cortes e transições rápidas, quase sempre munido de diálogos rápidos e afiados, tão cheios de significado que encheriam um livro sobre as implicações filosóficas de cada um deles.
Ao mesmo tempo, se analisarmos o filme do ponto de vista histórico, Kazan pinta um panorama preciso, mistura de lúdico com trágico, dos Estados Unidos durante a Segunda Guerra. Lúdico, pois usa na maioria das vezes as crianças e suas ações para dar uma espiada em como a sociedade se comportava à época da guerra e da depressão, uma época com grande aperto monetário e famílias lutando para sobreviver. Analisando sob esse aspecto, e sabendo que as pessoas tendem a criar seus mitos e suas ilusões (apenas para se sentirem bem) exatamente nessas épocas difíceis, o filme acaba sendo o eco de si mesmo, ou "que tipo de filmes as pessoas que viveram essa data gostariam de ver".
Ainda que use crianças quase sempre, há uma bela sequência que gira em torno de um poste a uma certa altura e se aproxima da esperançosa filha lendo o livro sugerido pela bibliotecária, para tornar seu sábado menos doloroso com a leitura de Agonia da Melancolia, pois a menina insiste em ler todos os livros da biblioteca em ordem alfabética, pois deseja reter "todo o conhecimento do mundo".
Porém, é preciso notar que o roteiro nunca parte para o maniqueísmo do choro fácil, o que no caso seria apenas questão de simplificar a história. Não. O roteiro insiste em tomar o caminho completo, complexo da psique humana, nem que para isso tenha que ferir o espectador (mas, ei, a família do filme sofre infinitamente mais, então é até covardia nos compararmos aos personagens desse drama).
O final, que também aparentemente leva o caminho fácil quando na verdade está usando da praticidade e até da realidade plausível, entrega de bandeja a conclusão inteligente de que, sejamos otimistas ou pessimistas, basta vivermos com o nosso melhor, que a vida fará o resto para nos ajudar.
E eu até gostaria de terminar este texto com uma das muitas frases memoráveis do filme, mas é tarefa ingrata escolher entre tantos exemplos tão ricos quanto cada cena cuidadosamente planejada desse clássico precoce de Elia Kazan.
# Cerejeiras em Flor
Caloni, 2011-10-29 <cinema> <movies> [up] [copy]Hanami conta a história de um casal que mantém uma vida pacata no interior da Alemanha enquanto mantém uma relação distante com seus três filhos, especialmente o caçula, que vive em Tóquio. O sonho da esposa é poder visitá-lo, pois, além da saudade, é visivelmente encantada pela cultura japonesa, como pode-se perceber pelos detalhes de decoração da casa deles e pelo seu interesse no butô, um estilo de dança teatral que utiliza a expressão do corpo e seu efeito na sombra formada pelos movimentos.
Assim como o butô, a direção de Doris Dörrie (Felicidade) trabalha sua narrativa de maneira sutil, desenhando e evoluindo as emoções do marido a partir da sombra de sua mulher, que sempre determina suas ações a partir de um momento-chave no longa. Para isso, é vital a entrega do ator Elmar Wepper, que compreende que viver passa a ter como função realizar os desejos de sua mulher, e daí a dicotomia da dança, que une marido e esposa como corpo e sombra (sendo que quem comanda os movimentos é justamente a sombra, na visão de uma dançarina de butô que surge no filme no segundo ato).
Hanami é o costume dos japoneses de observar a beleza das flores. Esse costume possui mais tradição na época em que as cerejeira florescem. No filme, a cerejeira desempenha um papel mais simbólico do que funcional, mas tem seus motivos, pelo menos filosóficos: ciente que não vai viver por muito mais tempo, o marido resolve como último impulso viver o resto de seus dias trazendo significado para a mulher, ainda que suas ações pareçam tão efêmeras, como a própria beleza das cerejeiras, que florescem em um determinado período do ano em abundância, mas logo desaparecem.
Esse simbolismo, aliás, também é usado na ideia de que é raro que o Monte Fuji apareça aos olhos humanos devido à névoa que cobre toda a região em volta. Porém, quando isso acontece, devemos aproveitar essa oportunidade e fazer tudo que devemos fazer.
Não é assim com a própria vida, tão efêmera, mas tão valiosa?
# Jovens Modernos
Caloni, 2011-10-29 <cinema> <movies> [up] [copy]Qual a visão de um crítico musical sobre a música contemporânea de vanguarda? Ou, uma pergunta ainda melhor: o que esse crítico pensa sobre os jovens dessa nova era, tão acomodados a ouvirem músicas de diversas correntes, muitas delas auto-proclamadas futuristas, e se limitarem a apertar o botão de curtir e compartilhar em sua rede social?
Essa questão não é respondida em Jovens Modernos, novo documentário de Jérôme de Missolz e que percorreu a meca de diversas correntes musicais das últimas décadas, tendo como seguidores supostos fãs do crítico (ou da música que este persegue).
Iniciando com a morte de um famoso cantor que aparentemente teria um brilhante futuro, mas que decidiu se matar logo cedo, o filme acaba se transformando muito mais em uma mescla e uma viagem por diversos estilos musicais, como rock, punk, techno, suas influências norte-americanas e uma retrospectiva do que isso significava para sua época e, o mais interessante, qual a visão daqueles tempos nos jovens de hoje.
A resposta é simples: o saudosismo de um tempo em que a criatividade estava a todo vapor e onde os jovens tinham pelo quê lutar (nem que fosse pela contracultura) gerava conteúdo de uma forma ou de outra. As tentativas de se expressar também fizeram parte do modo de se portar, de se vestir e até de se matar. E isso ocorria por muitos fenômenos durante as décadas de 80 e 90.
Dotado de uma ótima edição de vídeo e som, lembrando o igualmente ótimo Pink Floyd - The Wall, o filme desfila facilmente por diversas vertentes sem nunca soar repetitivo, mas acaba embutindo um sentimento que, ao mesmo tempo que soa anacrônico, é visivelmente datado, o que acaba por invalidar o fato de que este foi produzido nos tempos atuais.
O único resquício de atualidade repousa no último ato, onde crítico e seguidores pousam em Pequim, possível nova fonte artística, ou pelo menos de influência, dos artistas futuristas que Yves Adrien tanto estuda. A queda das torres gêmeas e o declínio econômico são citados en passant, em uma clara alusão à virada socio-econômica mundial, e como isso deve afetar o que será produzido desde então.
# Demônio
Caloni, 2011-10-30 <cinema> <movies> [up] [copy]O filme começa com uma narração em off (que nunca é revelada) a respeito de uma história contada pela avó do sujeito que dizia que o demônio, às vezes, "sobe à superfície" para pegar algumas almas desprevenidas. De acordo com a mesma avó, o demônio segue algumas regras, que se iniciam com um suicídio (nunca explicado no filme), que permite que ele entre e apronte mais uma das suas.
Com esse argumento superficial para não dizer bobo, o diretor Brian Nelson coloca personagens que, inicialmente interessantes pela forma com que são apresentados, são aos poucos esmagados pela assustadora falta de criatividade em conduzir uma história que possui tanto elementos sobrenaturais quanto uma suposta análise da psique humana.
A ideia central da trama é que os personagens, uma vez presos no elevador, vão ficando cada vez mais tensos conforme acontecimentos nunca revelados acabam por ir matando um a um. O interessante é que essas mortes vão ocorrendo estrategicamente quando a luz se apaga por alguns segundos, revelando não apenas uma das muletas do projeto como também sua maior falha: não há nada impactante em aguardar quem será a próxima vítima, uma vez que o próprio título já revela estarmos mexendo com forças sobrenaturais, e por isso de nada adiantaria descobrir a suposta pessoa que incorporou o ente do mal (o que fazer, se nenhum deles consegue sair do lugar onde estão presos, mesmo?).
A única coisa que resta, então, é seguirmos os passos da direção, que pelo menos mantém ângulos sempre interessantes, tanto dentro do elevador quanto ao descrever a ação que ocorre fora dele para manter o prédio sob controle e para resgatá-los. É interessante porque, ainda que os personagens nunca representem pessoas de carne e osso, mas sim estereótipos prontos para serem abatidos pela força-sobrenatural-título, a tensão acaba funcionando, pois, de uma forma ou de outra, não é uma situação que qualquer pessoa gostaria de estar, sendo até natural o filme nos deixar compenetrados.
Com uma conclusão boba, que sequer era esperada pelo espectador, Demônio acaba representando apenas um bom exercício de linguagem cinematográfica, exercício esse desempenhado muitas vezes melhor em obras inspiradas pelas mesmas "limitações técnicas", como O Cubo e Enterrado Vivo.
[2011-09] [2011-11]