| Wireguard reconfiguring AllowedIPs can cause issues 2024-05-16 [tag_english] [tag_coding] When reconfiguring Wireguard AllowedIPs list it could happen that previous or parallel connections (race condition) send/receive packets to/from forbidden IPs. This is not a problem if this connections are eventually closed. However, worth noticing. |
|
Tail recursion in loop while
2024-04-15 [tag_english] [tag_coding] Interesting optimization of recursion using tail function. Consider this: void RecursiveFunction(ref HashSet |
| Cognitive Complexity (SonarQube) 2024-04-15 [tag_english] [tag_coding] - Increment when there is a break in the linear (top-to-bottom, left-to-right) flow of the code. - Increment when structures that break the flow are nested. - Ignore "shorthand" structures that readably condense multiple lines of code into one. |
| WireGuard 2023-06-15 [tag_english] This is the VPN solution used in the project I am working on, a simple and secure packet distribution and controlled by the IP addresses configured for each peer. There is a very nice example in [the home of WireGuard project]. |
| Debugging a non signed driver in Windows 10 2023-06-15 [tag_english] [tag_debugging] [tag_coding] Not always just to disable driver signing enforcement work in Windows. In Windows 10 when tried to start a driver after reboot with `bcdedit -set TESTSIGNING ON` I still got the `StartService FAILED 577: Windows cannot verify the digital signature for this file` message. |
| Critical Sections and Outlook 2023-06-15 [tag_reversing] [tag_english] [tag_debugging] [tag_coding] Today was a happy crush analysis day, because I receive an Outlook memory dump the moment it frooze the main window in the beginning of the process. I asked for one because it could be useful to another analysis I was doing with Office server communication. |
| Asciidoc is the best 2023-06-05 [tag_coding] [tag_english] [tag_essays] After reading about the purpose and [current implementation of asciidoctor] I realize that asciidoc is the best text standard for the future of the blog. I say that based on the structure care of the format, the embebbed metadata into its own format and the clear objective of being a unique and formalized standard, what could simplify a lot the necessity of writers and publishers of keeping a text base as the original and yet keep the structure inside with almost no effort in the side of the writers. |
 Hacker Rank Array - Part 1
2023-04-28 [tag_english] [tag_interview] [tag_coding] The next step after [the Warm Up challenges] are the array challenges. And so I did it. Now I am going to recap what I did and how I did. And what complexity the algorithms have. # Array Manipulation
Hacker Rank Array - Part 1
2023-04-28 [tag_english] [tag_interview] [tag_coding] The next step after [the Warm Up challenges] are the array challenges. And so I did it. Now I am going to recap what I did and how I did. And what complexity the algorithms have. # Array Manipulation
|
 Miniature with hidden tactic
2023-03-04 [tag_chess] [tag_english] White move and gain advantage. image::board.png[] 1. Nf3 e6 2. e4 h6 3. d4 a6 4. Nc3 b5 5. a3 c5 6. Be3 {Three pieces already developed and the adversary has none.} 6... cxd4 7. Nxd4 Bb7 8. f3 Nf6 9. Bd3
Miniature with hidden tactic
2023-03-04 [tag_chess] [tag_english] White move and gain advantage. image::board.png[] 1. Nf3 e6 2. e4 h6 3. d4 a6 4. Nc3 b5 5. a3 c5 6. Be3 {Three pieces already developed and the adversary has none.} 6... cxd4 7. Nxd4 Bb7 8. f3 Nf6 9. Bd3
|
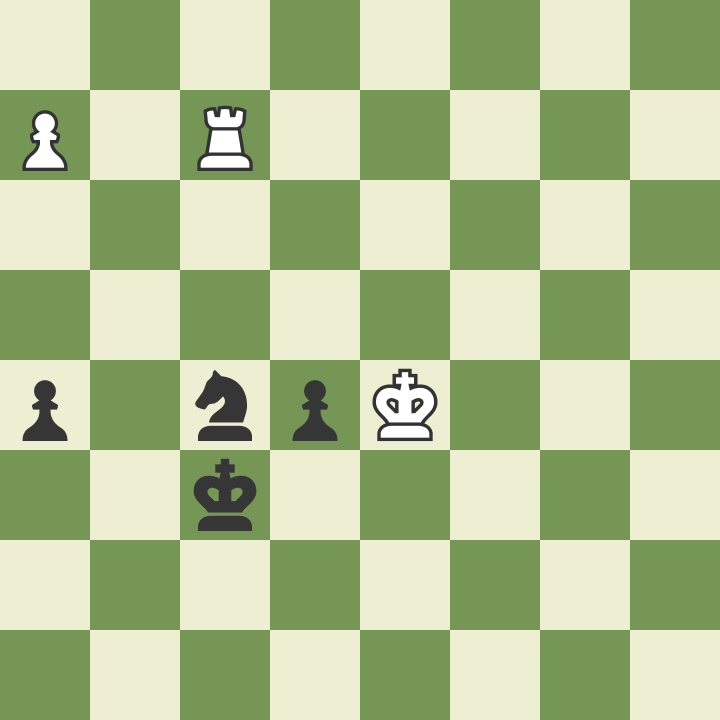 White move and win the game
2023-02-26 [tag_chess] [tag_english] A game with ups and downs. Entirely asymmetrical. White move and win the game. image::board.png[] 1. e4 c5 2. d4 cxd4 3. c3 dxc3 4. Nxc3 b6 5. Bc4 Bb7 6. Nf3 Nc6 7. Bf4 e6 8. Nb5 Rc8 9. Bd6 a6 10. Bxf8 axb5 11. Bxg7 bxc4 12. Bxh8 f6 13. e5 Nxe5 14. Nxe5 Bxg2
White move and win the game
2023-02-26 [tag_chess] [tag_english] A game with ups and downs. Entirely asymmetrical. White move and win the game. image::board.png[] 1. e4 c5 2. d4 cxd4 3. c3 dxc3 4. Nxc3 b6 5. Bc4 Bb7 6. Nf3 Nc6 7. Bf4 e6 8. Nb5 Rc8 9. Bd6 a6 10. Bxf8 axb5 11. Bxg7 bxc4 12. Bxh8 f6 13. e5 Nxe5 14. Nxe5 Bxg2
|
 Ups and downs
2023-02-26 [tag_chess] [tag_english] White moves and win. image::board1.png[] Now black moves and win. image::board2.png[] Black moves and win (but they prefer to lose instead). image::board3.png[] 1. Nf3 d5 2. e4 dxe4 3. Ng5 Bf5 4. Nc3 Nf6 5. Qe2 Nc6 6. Ngxe4 Nxe4 7. Nxe4 e5
Ups and downs
2023-02-26 [tag_chess] [tag_english] White moves and win. image::board1.png[] Now black moves and win. image::board2.png[] Black moves and win (but they prefer to lose instead). image::board3.png[] 1. Nf3 d5 2. e4 dxe4 3. Ng5 Bf5 4. Nc3 Nf6 5. Qe2 Nc6 6. Ngxe4 Nxe4 7. Nxe4 e5
|
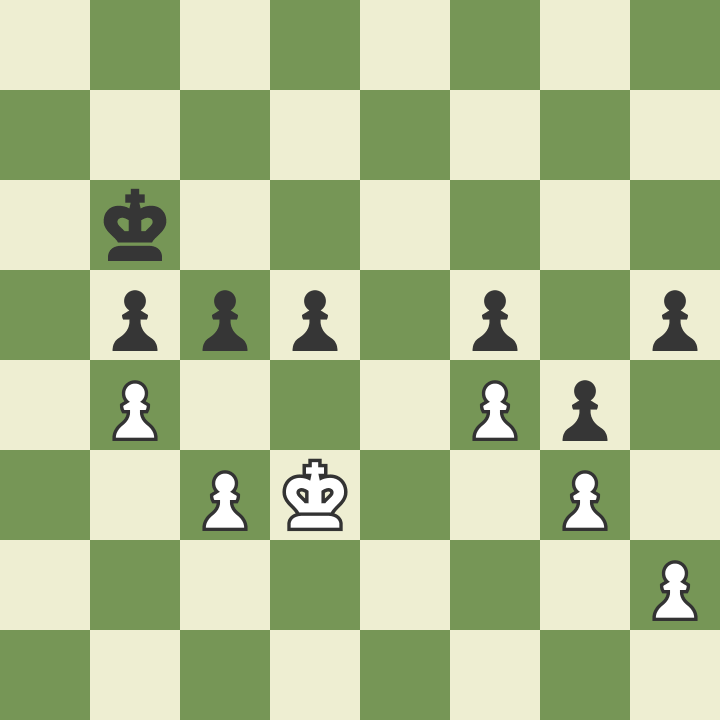 Keep the advantage in pawn and king final
2023-02-24 [tag_chess] [tag_english] Black to move and to keep the advantage there is a much instructive little plan to execute. image::board.png[] 1. Nf3 d5 2. e4 dxe4 3. Ng5 Nf6 4. Bc4 e6 5. O-O h6 6. Nh3 Bd6 7. d3 exd3 8. Bxd3 O-O 9. Bf4 Nc6 10. Nc3 Be5 11. Re1 Bxf4 12. Nxf4 Nd5 13. Nfe2 Ne5 14. Bb5
Keep the advantage in pawn and king final
2023-02-24 [tag_chess] [tag_english] Black to move and to keep the advantage there is a much instructive little plan to execute. image::board.png[] 1. Nf3 d5 2. e4 dxe4 3. Ng5 Nf6 4. Bc4 e6 5. O-O h6 6. Nh3 Bd6 7. d3 exd3 8. Bxd3 O-O 9. Bf4 Nc6 10. Nc3 Be5 11. Re1 Bxf4 12. Nxf4 Nd5 13. Nfe2 Ne5 14. Bb5
|
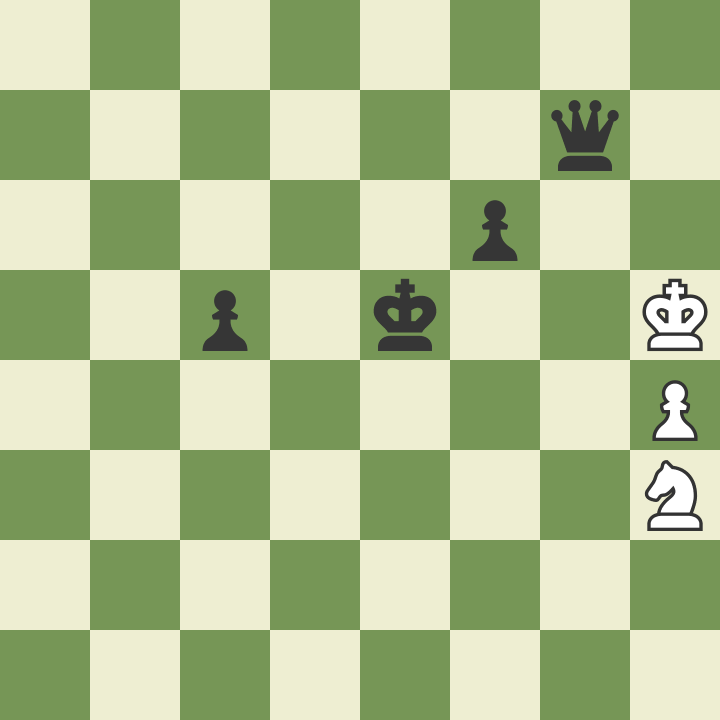 Let's go to the final with one horse
2023-02-20 [tag_chess] [tag_english] Black moves and it is M1 after that. image::board.png[] 1. d4 g6 2. Nf3 Bg7 3. e4 e6 4. e5 d6 5. Bg5 Ne7 6. Nc3 dxe5 7. dxe5 O-O {Suddenly I am lost.} 8. Qxd8 Rxd8 9. Bxe7 Rd7 10. Bf6 b6 11. Be2 Bb7 12. O-O
Let's go to the final with one horse
2023-02-20 [tag_chess] [tag_english] Black moves and it is M1 after that. image::board.png[] 1. d4 g6 2. Nf3 Bg7 3. e4 e6 4. e5 d6 5. Bg5 Ne7 6. Nc3 dxe5 7. dxe5 O-O {Suddenly I am lost.} 8. Qxd8 Rxd8 9. Bxe7 Rd7 10. Bf6 b6 11. Be2 Bb7 12. O-O
|
 Please keep the advantage
2023-02-19 [tag_chess] [tag_english] You are black and need to keep the advantage. What do you do? image::board1.png[] White move and M4. Can you see it? image::board2.png[] 1. e4 c5 2. Nf3 Nc6 3. Bc4 e6 4. O-O g6 5. Re1 Bg7 6. d3 Nge7 7. a3 O-O 8. e5
Please keep the advantage
2023-02-19 [tag_chess] [tag_english] You are black and need to keep the advantage. What do you do? image::board1.png[] White move and M4. Can you see it? image::board2.png[] 1. e4 c5 2. Nf3 Nc6 3. Bc4 e6 4. O-O g6 5. Re1 Bg7 6. d3 Nge7 7. a3 O-O 8. e5
|
 Hidden tactic
2023-02-18 [tag_chess] [tag_english] There a tactic move here hidden. White move and get instant material. image::board.png[] 1. Nf3 c5 2. e4 d5 3. exd5 Qxd5 4. Nc3 Qe6+ 5. Qe2 Nf6 6. Nb5 Na6 7. d4 cxd4 8. Nfxd4 Qxe2+ 9. Bxe2 e5 10. Nf3 e4 11. Nfd4 Bd7 12. Be3 Bxb5 13. Nxb5 Be7 14.
Hidden tactic
2023-02-18 [tag_chess] [tag_english] There a tactic move here hidden. White move and get instant material. image::board.png[] 1. Nf3 c5 2. e4 d5 3. exd5 Qxd5 4. Nc3 Qe6+ 5. Qe2 Nf6 6. Nb5 Na6 7. d4 cxd4 8. Nfxd4 Qxe2+ 9. Bxe2 e5 10. Nf3 e4 11. Nfd4 Bd7 12. Be3 Bxb5 13. Nxb5 Be7 14.
|
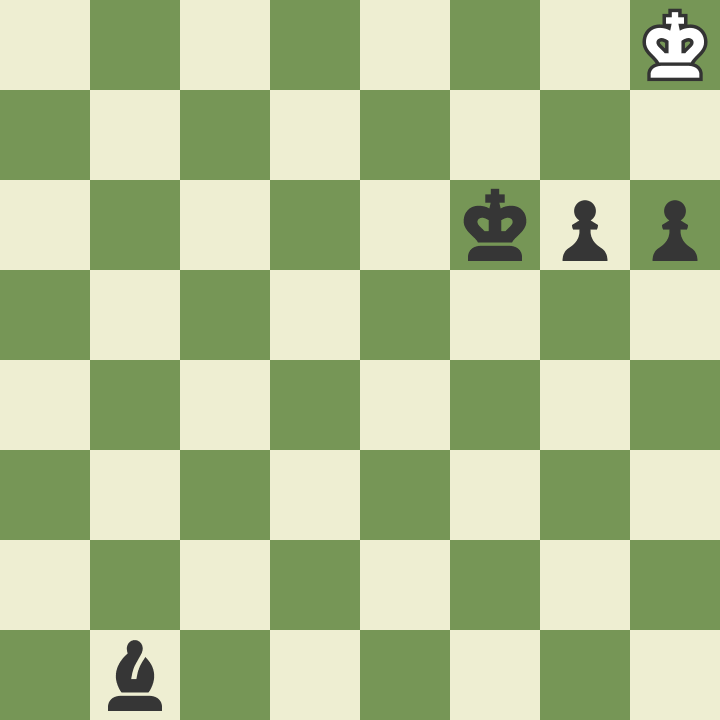 Decided to draw a won game
2023-02-18 [tag_chess] [tag_english] I could move (black) and M2, but I decided to draw =P. image::board.png[] 1. d4 Nf6 2. Bf4 g6 3. Nf3 Bg7 4. e3 O-O 5. c3 Re8 6. Bd3 d6 7. e4 Nbd7 8. e5 dxe5 9. Nxe5 Nd5 10. Bg3 Nxe5 11. Bxe5 Bxe5 12. dxe5 e6 13. Bc4 c6 14. Nd2 Bd7
Decided to draw a won game
2023-02-18 [tag_chess] [tag_english] I could move (black) and M2, but I decided to draw =P. image::board.png[] 1. d4 Nf6 2. Bf4 g6 3. Nf3 Bg7 4. e3 O-O 5. c3 Re8 6. Bd3 d6 7. e4 Nbd7 8. e5 dxe5 9. Nxe5 Nd5 10. Bg3 Nxe5 11. Bxe5 Bxe5 12. dxe5 e6 13. Bc4 c6 14. Nd2 Bd7
|
 Unsuspicious of forks
2023-02-17 [tag_chess] [tag_english] I am not proud of this game, but it has some interesting highlights. By example, black move knight and has a unexpected fork in exchange. image::board1.png[] And... I wasn't aware of this triple fork (can you believe it?). Black moves again and screw it up.
Unsuspicious of forks
2023-02-17 [tag_chess] [tag_english] I am not proud of this game, but it has some interesting highlights. By example, black move knight and has a unexpected fork in exchange. image::board1.png[] And... I wasn't aware of this triple fork (can you believe it?). Black moves again and screw it up.
|
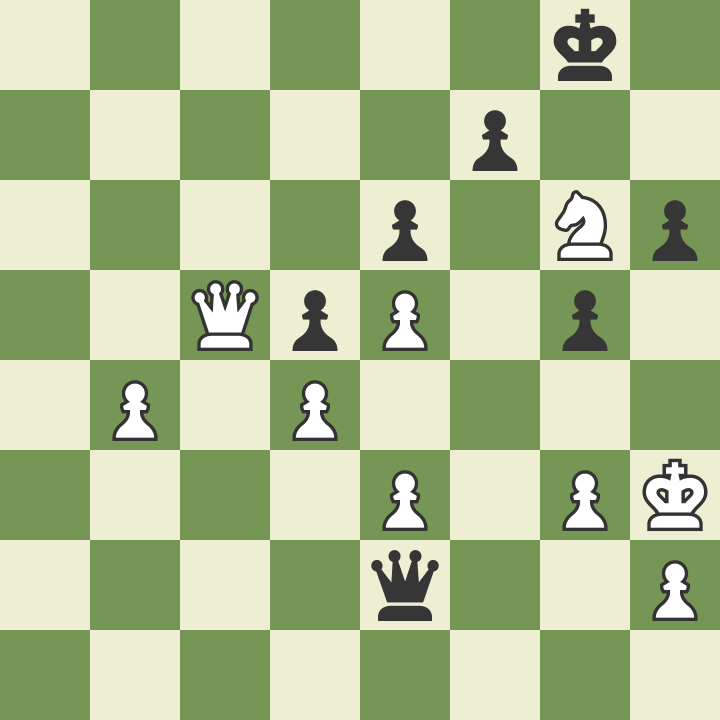 King exposure is the key to victory
2023-02-15 [tag_chess] [tag_english] White plays and keep advantage. image::board1.png[] And now... black move and M4. image::board2.png[] 1. Nf3 e6 2. e4 h6 3. d4 d6 4. b3 a6 5. Bb2 Nc6 6. g3 Nf6 7. Nbd2 Be7 8. Bg2 O-O 9. O-O Re8 10. Re1 Bf8 11. c4 d5 12. e5 Nd7 13. c5 b6 14. cxb6 Nxb6 15. Rc1 Nb4
King exposure is the key to victory
2023-02-15 [tag_chess] [tag_english] White plays and keep advantage. image::board1.png[] And now... black move and M4. image::board2.png[] 1. Nf3 e6 2. e4 h6 3. d4 d6 4. b3 a6 5. Bb2 Nc6 6. g3 Nf6 7. Nbd2 Be7 8. Bg2 O-O 9. O-O Re8 10. Re1 Bf8 11. c4 d5 12. e5 Nd7 13. c5 b6 14. cxb6 Nxb6 15. Rc1 Nb4
|
| Close Remote Socket 2020-07-05 [tag_english] [tag_coding] I got used to close sockets in Windows using TCP View, but I haven't learned yet how to do this in Linux. Some Google and now I know. It is kinda simple in terminal mode, as any task a programmer needs to do in your system. |
| Some things I learned in a Hacker Rank exercise 2019-08-08 [tag_english] [tag_ccpp] [tag_coding] A couple of days ago I subscribed to Hacker Hank, a website specialized in provide interview exercises. The site is as a better version of Code Jam, with the possibility to Compile & Run the code, as well as running several test cases. |
| Real Programmers Don't Use Java 2014-02-20 [tag_english] When I was a newbie (and a wanna-be) I enjoyed reading "Real Programmers Don't Use Pascal", a satiric text that influenced and encouraged me into the path of "C/C++ enlightenment", most even than K&R's book. Since then I thought that being a "Real Programmer" was something close to everything one needs to know to get (hard) things done (quickly). Being a "Quiche Eater" was, in couterpart, comparable to nothing. Real Programmers solve real problems! Quiche Eaters are losers who study the academic concepts of computer science and never do a damn useful and/or working program (maybe you know some guy like this). |
| Using TodoList and Microsoft Project together 2010-04-10 [tag_english] [tag_coding] The next article about bits is still in the oven. Taking vacation (40 days) had drop me out of ideas! At the moment, I can explain the tips and tricks using TodoList to manage my team and synchronize my tasks in a Microsoft Project timesheet. |
| What I've been doing in the last 10 years 2009-08-17 [tag_english] This week I dedicate myself to update my resumè and I have the brilliant idea of put into it my technical historical, what resuming is a list of things I did or was involved with during my brief ten years stay in the programming world. |
| Static Polymorphism 2009-07-10 [tag_english] [tag_coding] To explain the polymorphism nothing is better than see how stuff used to be. If you were a twenty old C programmer in the past and created the following functions: int soma(int x, int y); double soma(double x, double y); |
 How to run anything as a service
2008-05-27 [tag_english] [tag_coding] The biggest advantage running an application as a service, interactive or not, is to allow its start before a logon be performed. An example that happens to me is the need of debugging a [GINA]. In order to do this, I need the Visual Studio remote debugger be started before logon. The easiest and fastest solution is to run Msvcmon, the server part of debugging, as a service.
How to run anything as a service
2008-05-27 [tag_english] [tag_coding] The biggest advantage running an application as a service, interactive or not, is to allow its start before a logon be performed. An example that happens to me is the need of debugging a [GINA]. In order to do this, I need the Visual Studio remote debugger be started before logon. The easiest and fastest solution is to run Msvcmon, the server part of debugging, as a service.
|
| Funky do-while 2008-02-13 [tag_english] [tag_coding] It's a known habit to use do-while constructions when there's a need to define a macro that has more than one command instead of using the { simple multicommand brackets }. What was never clear is why this is so. |
 Silly regex trick
2008-02-07 [tag_english] [tag_coding] I know what you going to think about this one: "silly trick". That's why I just put it in the title. Anyway, that is something I use everyday, so I thought it might be useful to who cares about productivity.
Silly regex trick
2008-02-07 [tag_english] [tag_coding] I know what you going to think about this one: "silly trick". That's why I just put it in the title. Anyway, that is something I use everyday, so I thought it might be useful to who cares about productivity.
|
| MouseTool 2007-11-13 [tag_english] Well, as most of you already know, I really don't like mice. Nevertheless I respect the users who use it and like it. That is the reason why I am writing a little more about it. This time, I going to show a program I use every day: MouseTool, for the users who does not use the mouse and like it. |
| Why is my DLL locked? 2007-09-24 [tag_english] [tag_coding] The Windows code responsible to call DllMain for each loaded and unloaded DLLs uses an exclusive access object, the so-called mutex, to synchronize its calls. The result is that inside a process just one DllMain can be called at a given moment. This object-mutex is called "loader lock" into the Microsoft documentation. |
| C and C++ Operators Precedence Table 2007-07-30 [tag_english] [tag_ccpp] [tag_coding] > Wanderley, your explanation about [why a program compiles in C++ and not in C] seems to me logic and correct, but gave me some doubts, because I always learned that the C and C++ operator precedence are the same thing. I checked out the Appendix A in the "C ++ - How To Program" (sixth edition) and the book table is equal to the C operators precedence table and it is different from the C++ precedence table presented by you in the article. I went to the internet and found out in two websites the table and both are equal to the book table: |
| What happens inside the sizeof operator 2007-07-16 [tag_english] [tag_ccpp] [tag_coding] The question: how to get the size of a struct member without declaring it as a variable in memory? In pseudocode: static const size_t FIELD_SIZE_MSGID = 15; struct FEEDER_RECORD_HEADER { |
|
Precedence difference
2007-07-10 [tag_english] [tag_ccpp] [tag_coding] Once upon a time my old friend Kabloc wrote this little and "harmless" function in order to print the multiplication table: #include |
| Google shortcuts 2007-07-06 [tag_english] I love shortcuts. Since my very first years using computers, shortcuts had become my obsession. I research them through the time, collecting them, using them. For a long time I avoid myself from touching the mouse, trainning to remember all keystroke sequences I know. |
| Disassembling the array operator 2007-06-22 [tag_english] [tag_ccpp] [tag_coding] Arrays are fascinating in C language because they are so simple and so powerful at the same time. When we start to really understand them and realize all its power we are very close to understand another awesome feature of the language: pointers. |